Blog
Unlock your potential to become a cybersecurity expert by consuming quality content.
What is DLL Hijacking and How to Prevent it?
Offensive Security
In this article, we will explore DLL Hijacking, and how attackers use it for privilege escalation in...
Introduction to Malware Analysis
Defensive Security
In this article, we will try to learn what malware is and how malware analysis works. It is aimed at...
Create Bind and Reverse Shells using Netcat
Offensive Security
Netcat (nc, ncat, or the swiss army knife of networking, as some might prefer to call it) ...
Server-Side Request Forgery (SSRF) Explained
Offensive Security
Server-Side Request Forgery (or SSRF) is an attack that consists of inducing a web applica...
Host Header Injection Attacks
Offensive Security
Host Header injection is not the type of attack that you would normally find in CTFs or security cha...
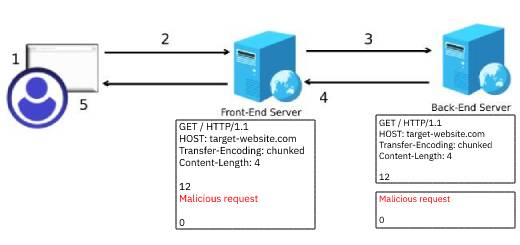
HTTP Request Smuggling Explained
Offensive Security
HTTP Request Smuggling (HRS) is a type of attack that is gaining more and more attention in rec...
XXE Attacks Explained
Offensive Security
Out of the many attacks that threaten web applications today, XXE remains the one that is ...
CSRF (Cross-Site Request Forgery) Explained
Offensive Security
Cross-Site Request Forgery (CSRF or XSRF), also called Client-Side Request Forgery, i...
Introduction to Cross-Site Scripting (XSS)
Offensive Security
This article presents a great introduction for anyone trying to learn about Cross-Site Scripting (or...
Using THC Hydra To Brute Force Login Forms
Offensive Security
THC Hydra is a powerful tool to use against login forms. It can perform brute force and diction...
Linux Privilege Escalation: Three Easy Ways to Get a Root Shell
Offensive Security
Once you’ve gained access to a Linux system, the next logical step is to perform&nbs...
Using John The Ripper To Crack Password Hashes
Offensive Security
Every self-respecting pentester should have a powerful password cracker in their toolkit, and John t...
Using Gobuster to Find Hidden Web Content
Offensive Security
Directories and Files enumeration is one of the first steps that an attacker performs during web app...
Introduction to SQL Injection
Offensive Security
SQL injection is often referenced as the most common type of attack on websites. It is being used ex...
How To Use Nmap: A Beginner’s Guide
Offensive Security
Nmap is an open-source network mapping tool developed by Gordon Lyon. It is widely used as a po...
Overthewire, Learn Hacking By Playing Games
Offensive Security
If you’ve spent enough time on the web searching for practical resources to learn how to hack,...
Google Dorks Explained
Offensive Security
Whenever you want to look for something on the Internet, you use Google. The giant search engine ind...